Why Security Matters When AI Becomes Infrastructure
When an AI system moves from “answering questions” to executing real actions, security stops being optional.
Openclaw is not a chatbot.
It can deploy services, manage containers, access repositories, and operate continuously.
That power changes the threat model entirely.
The goal is not to make Openclaw “perfectly secure”, which does not exist.
The goal is to make its attack surface explicit, minimal, and auditable.
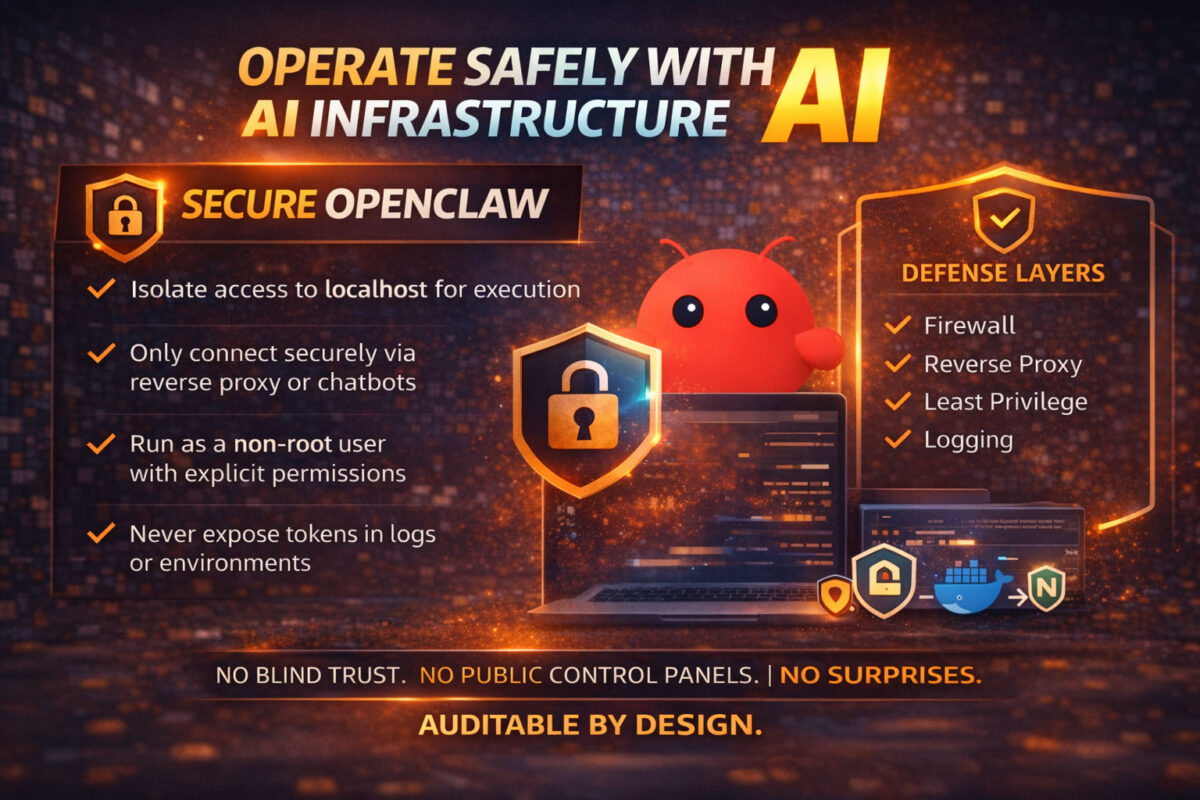
Openclaw’s Security Model at a Glance
Openclaw is designed around a few non-negotiable principles:
- No implicit access
- No exposed control panels by default
- No public APIs unless you create them
- No dependency on vendor-controlled infrastructure
Everything runs on your server, under your rules.
Security is achieved through architecture, not obscurity.
Network-Level Isolation Comes First
The most common failure in self-hosted AI agents is accidental exposure.
Openclaw avoids this by design:
- The agent does not expose a public web interface by default
- Internal services bind to
localhost, not0.0.0.0 - External access happens through:
- Messaging platforms (Telegram, WhatsApp)
- A reverse proxy when explicitly configured
In a typical setup:
- Only ports 80 and 443 are exposed publicly
- All execution endpoints remain internal
- No direct TCP access to the agent exists from the internet
This alone eliminates most real-world attacks.
Reverse Proxy Is a Gate, Not a Shield
A reverse proxy such as Nginx Proxy Manager plays a critical role, but it is not magic.
What it does well:
- Terminates HTTPS
- Centralises certificates
- Prevents direct exposure of internal services
What it does not do:
- Protect non-HTTP traffic
- Filter UDP or random TCP ports
- Replace a firewall
That is why Openclaw setups should always assume:
- The proxy is a routing layer
- The firewall is the actual perimeter
Security works when both exist.
Execution Permissions Are Explicit and Local
Openclaw does nothing unless you allow it to.
Key characteristics:
- All integrations are opt-in
- Credentials are stored locally
- The agent cannot “discover” new access on its own
- You decide which tools it can invoke
If Openclaw can:
- Access Docker
- Commit to GitHub
- Read a filesystem
That is because you explicitly allowed it.
This makes security decisions visible and reversible.
Why Self-Hosting Is Safer Than SaaS for This Use Case
A cloud AI service with execution capabilities would require:
- Permanent API access
- Broad permissions
- External trust boundaries
- Black-box logging and memory
With Openclaw:
- Memory stays on your disk
- Logs stay on your server
- Execution happens locally
- Nothing leaves the system unless you send it
You trade convenience for control, and in infrastructure, control is security.
Common Misconceptions About AI Agent Risk
“If the AI is powerful, it must be dangerous.”
Power is not the risk, unbounded access is.
“If it runs as a user, it’s unsafe.”
Running as a non-root user with explicit permissions is exactly the point.
“If it listens on a port, it’s exposed.”
Listening on localhost is not exposure. Binding to the public interface is.
Most real incidents come from misconfiguration, not from the agent itself.
Practical Hardening Without Overengineering
A secure Openclaw setup does not require enterprise paranoia.
Baseline best practices:
- Firewall default-deny incoming
- Only expose 80/443 publicly
- SSH with keys only
- No Docker containers publishing random ports
- Periodic review of permissions granted to the agent
This keeps the system predictable and understandable.
Security as a Continuous Relationship
Running an AI agent as infrastructure is not a “set and forget” decision.
It is a relationship:
- You grant access
- You observe behaviour
- You adjust boundaries
- You revoke when needed
Openclaw supports this model because it does not hide its actions behind abstractions.
Everything it does can be inspected.
Final Thoughts
Openclaw is safe when treated like infrastructure, not a toy.
If you:
- Control the network
- Limit exposure
- Understand permissions
- Own the runtime
Then an AI agent becomes no more dangerous than any other automation system.
The difference is not that it thinks.
The difference is that you decide what it is allowed to do.
And that is where real security lives.